TL;DR
Wanncry is type of malicious ransomware worm designed to block access to a computer system until a sum of ransom paid to creator. Infected systems include all desktop and server versions of Microsoft WINDOWS.
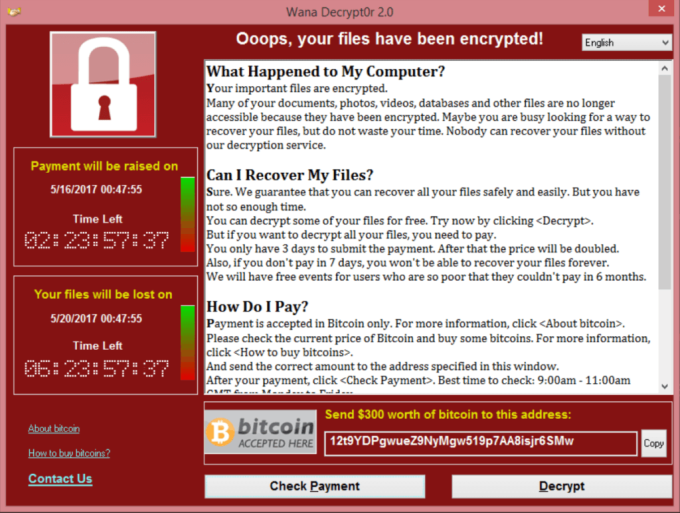
- WannaCry also known as WannaCrypt decryptor
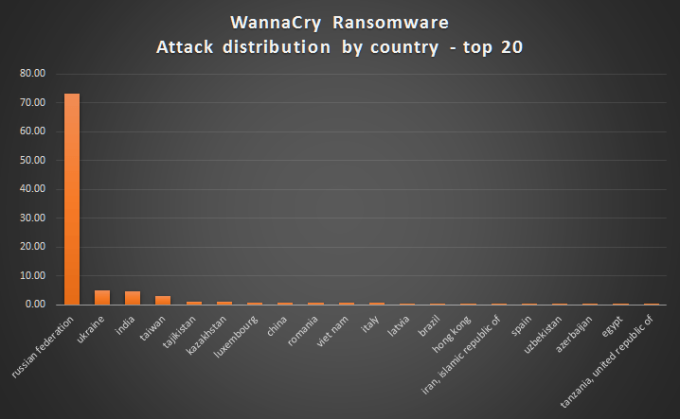
Who are infected by WannaCry till date ?
The worst-hit countries are like Russia, Ukraine, India and Taiwan. (USA?)
- List of affected countries (May 14, 2017)
What the heck is worm and ransomware?
A computer worm is a self-replicating computer program that penetrates an operating system with the intent of spreading malicious code.
Ransomware is a sophisticated piece of worm that blocks the victim’s access to victim's files and the only way to regain access to the files is to pay a ransom. Technically, it encrypt your files and folders with strong encryption methods which are mathematically impossible to decrypt.
Is the WannaCry is first ransomware attack? Are there any past experiences faced by industry?
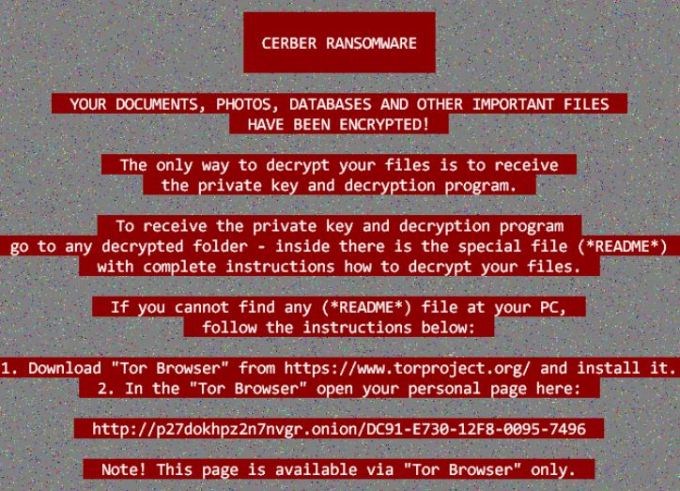
No. WannaCry isn’t the first one, first ransomware was noticed at mid-2005 which was beginning of more sophisticated encryption schemes with distributed efforts. In Dec 2016, before WannaCry, Cerber ransomware came along affecting millions systems through direct installation of execution files. (Many of RITans were affected too ! :O)
- Wallpaper changed by cerber ransomware attack !
Who are the creator of WannaCry ransomware ?
In April 20, Whistleblower group Shadow Broker leaked NSA’s zero day exploit for Server Message Block (SMB) called EternalBlue. The Sever Message Block provides shared access to files systems, printers and serial ports to carry out communications. For example, your nearest ATM is having shared access among other ATMs via this SMB protocol. This main exploit was about remote code execution in SMB which give access to victims system without password or special software installation. Many researchers asserted that WannaCry uses same exploit with some offensive additions.
None of the hacking groups claimed attack yet thus the creators of WannaCry are still anonymous and there is no way to find them as they are getting paid from bitcoins and having data node through TOR networks.
How much ransom they want ?
$300, the price can double if the amount isn't paid within 24 hours. Law enforcement officials have discouraged people from paying these ransoms although $60,000 already been paid.
Why they use bitcoin as payment method ?
Bitcoin is a cryptocurrency and a digital payment system which trades on daily basic (like stock market). All bitcoin transactions are stored publicly on the network, however, the identity of the user behind an address remains anonymous.

How many versions WannaCry have currently ?
There are two version of WannaCry spreading throughout the world.
- Wannacrypt 1.0 (With killswitch)
- Wannacrypt 2.0 (Without killswitch)
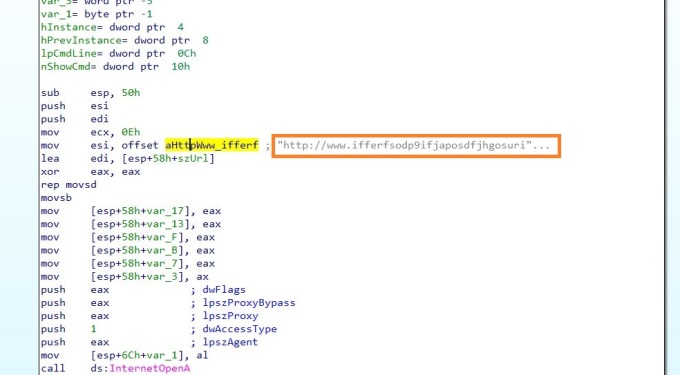
What is killswitch in system security ? (*Most valuable question)
The kill switch is kind of hardcoded mechanism/logic in case the creator wanted to stop it spreading. In 1.0, kill switch was URL
- URL kill switch of WannaCry 1.0 (coded into assembly language)
22-Year old security researcher from Britain found kill switch while he was on vacation, he claimed this domain name with $10 and accidentally stopped WannaCry 1.0. But next day, anonymous creator came up with another version 2.0 with no kill switch, hence it is spending desperately. (CNN News)
How this WannaCry propagating ?
- via Human interaction - like you download binary execution file (.exe) and allow permission to installing it.
In common cases, many among us download computer game cracks, software activator from internet. In this cases you might get ransomware instead of crack and on installation it may get triggered.
Another ways with phishing mails, many email providers block .exe files so propagators usually send you .doc file contain CSV injection vulnerability or .js file which execute JavaScript to download .exe file on your system.
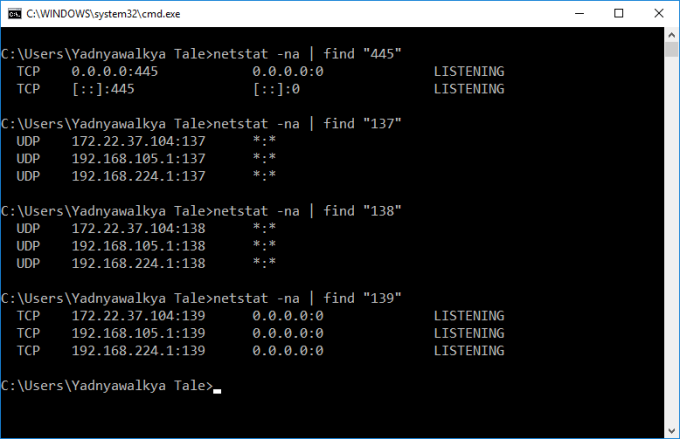
- via Open port (without interaction) - As mentioned above, this exploit is based on remote code execution so if you are having any of this open ports (445/137/138/139), you will get infected automatically (Means, you don’t need to do anything, just open port for public and boom !!! )
- netstat -na | find "port" command used to find open port
How does I know I'm affected or not ?
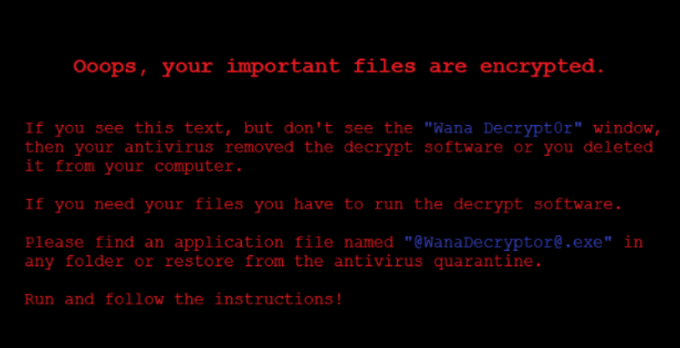
If your WINDOWS wallpaper hasn't changed to something like following, then you are not affected yet.
- Common behavior of WannaCry change wallapaper to this as a first stage
What should I do to prevent my system from WannaCry?
- Close open ports -
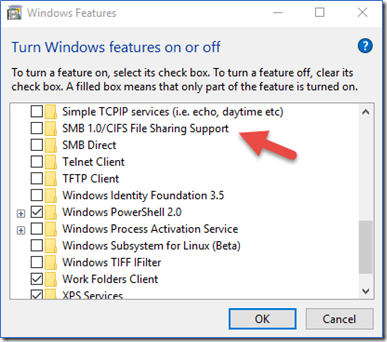
- Open command line (WIN+R) type optionalfeatures and hit return,
- In Window feature, uncheck SMB 1.0/CIFS File Sharing Support.
- Uncheck this SMB option
- Update your WINDOWS operating system - Update your WINDOWS manually. You can also download and install latest SMB patch from Microsoft MS17-010 update. Microsoft had already closed XP/VISTA support so if you are still using those OS then only god is going to save you !
- Stop installing untrusted execution files
- Install antivirus and scan your PC for virus.
OR
Leave WINDOWS, Start using Linux !
Why WannaCry only attacks on window? Why not Mac or Linux ?
This have strong technical reasons -
- Privileges - WINDOWS based on direct execution with equal privileges on other hand Linux and Mac (based on UNIX) have types of users and do not usually have such root (superuser) privileges for each execution, and hence they are safer than WINDOWS.
- Package Managers and Software Repositories - When you want to install a new program on your Windows desktop, you head to Google and search for the program. When you want to install most programs on Linux, you open your package manager and download it from your Linux distribution’s software repositories. These repositories contain trusted software that has been vetted by your Linux distribution – users aren’t in the habit of downloading and running arbitrary software.
My final conclusion of this article, WINDOWS is getting unsafe day by day with new attacks, loophole and 0days. You need to be stand on your own and to do that we, opensource community will help you ! Join RIT Redhat Academy to learn linux.
(We are happy to help you, change your OS to LINUX, contact any member of Redhat Academy)
LINUX IS SAFER, LINUX IS FUTURE !!!
No comments:
Post a Comment